Secure Access
With Session Monitoring &
AI-Powered Breach Prevention








the most comprehensive access platform for
your Admins, DevOps,
and Third Parties.
Agentless Access that Engineers love
With Fudo, users can get access to Unix/Windows servers, applications and devices quickly and easily. Users will not have to change their habits and can continue to use native clients like Unix Terminals, RDCMan, or Putty. They can also connect through the Fudo Web Client which only needs a web browser for access.

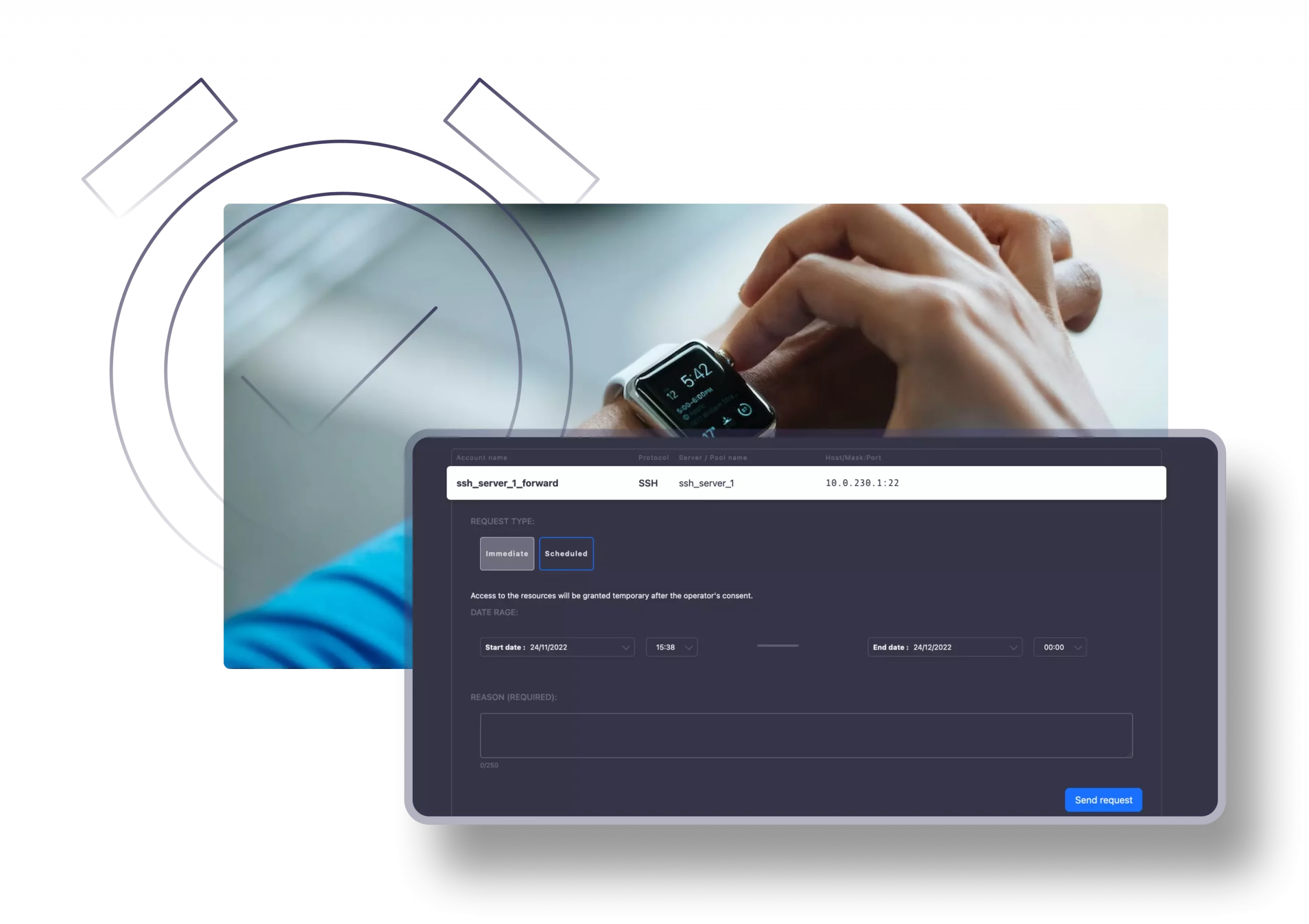
Just-in-Time
Using the JIT feature, you can create access workflows that adhere to the Zero-Trust approach. Through the request management section, you can easily define and schedule when a specific resource is available to a certain user and control it accordingly.
Cutting-edge session
monitoring & recording
Fudo allows you to permanently monitor and record all the ongoing sessions for 10+ protocols, including SSH, RDP, VNC, and HTTPS. You can watch the session live or use the footage for post-mortem analysis. Both the server and end user computers do not require any agents. Furthermore, Fudo offers the ability to join the session, sharing, pausing, and terminating, as well as great tools like OCR and tagging for better searching capabilities.

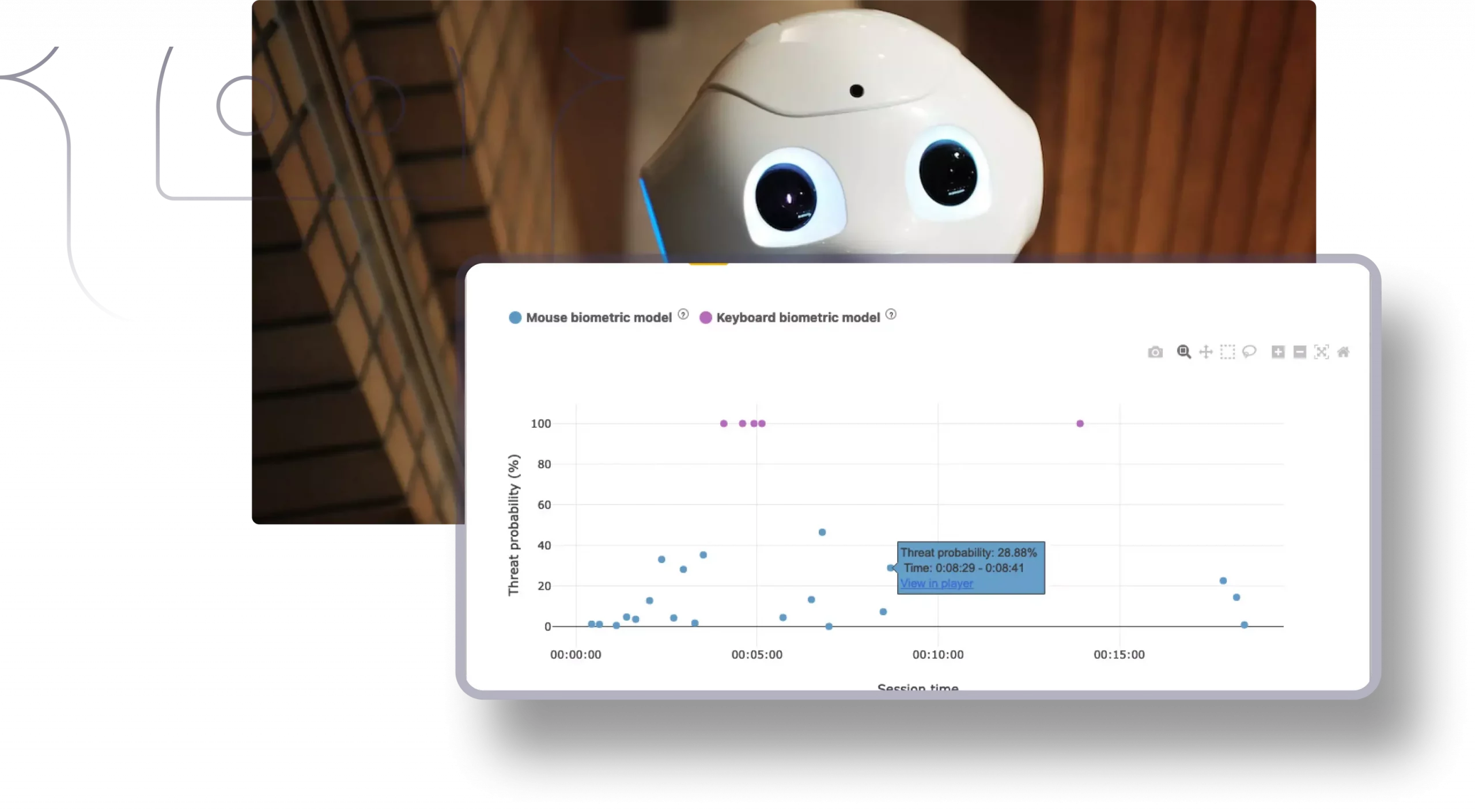
AI-Driven Breach Prevention
AI will assist CISOs in their day-to-day responsibilities by providing necessary guidelines and easing the verification and monitoring process. According to behavioral and semantic schemes interpreted by the system, you will be notified once a session is identified as suspicious.
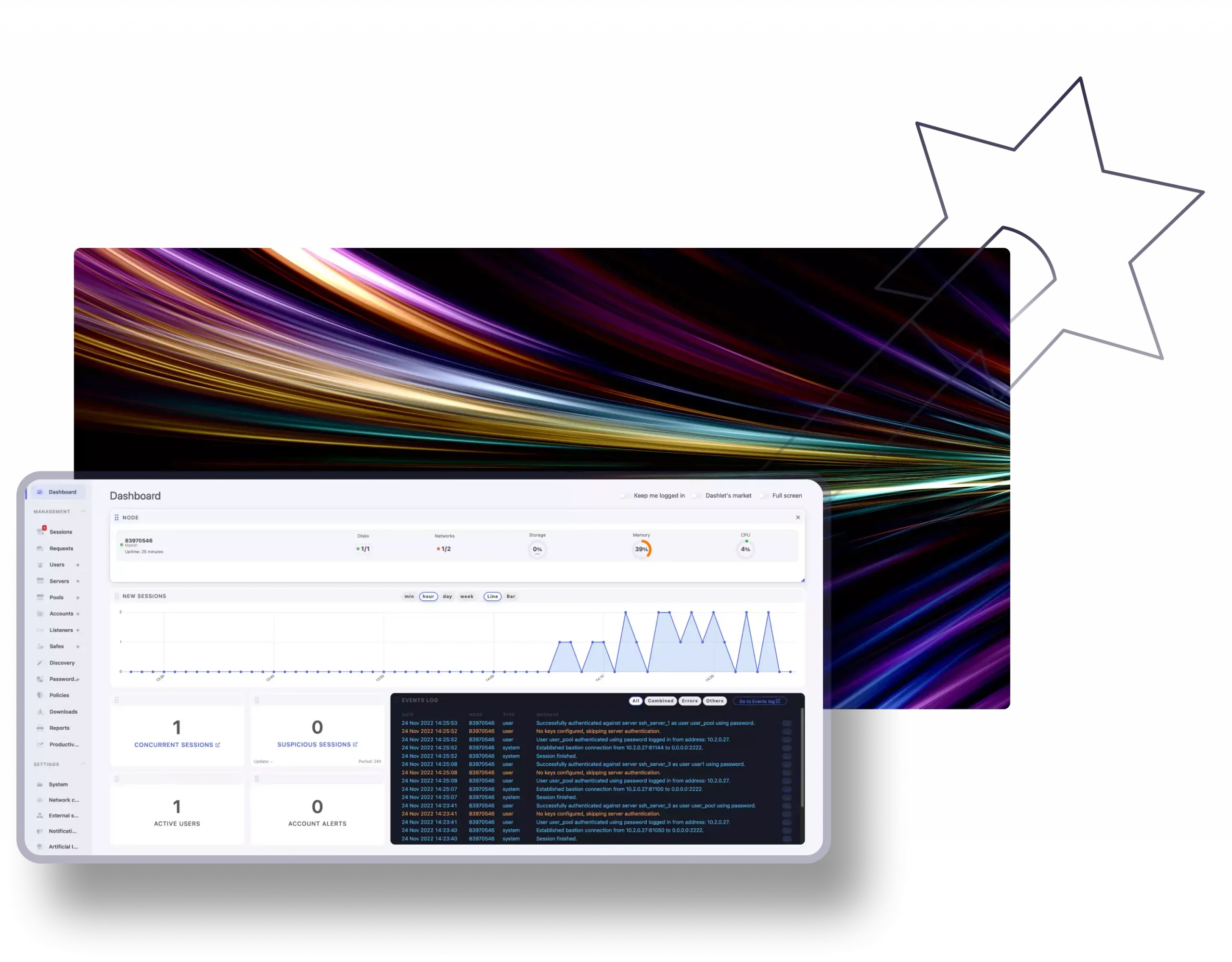
Rapid deployment
As a company, our top priority is to uphold all aspects of our mission competently, meticulously, and fluently. Fudo is an All-In-One solution, which means there are no additional costs nor subsidiary software required to initiate your own instance. Everything you will need is guaranteed within the core of either the appliance or the virtual machine, and guess what—the installation process can be finalized in literally one day.

your
TO

With the introduction of Fudo, we were able to offer our service
providers safer and more efficient connections to our servers.
ALBRECHT DURER AIRPORT NURNBERG
Marcus Gabriel
With the introduction of Fudo, we were able to offer our service providers safer and more efficient connections to our servers. The intelligent interface ensures a clear overview. Dealing and working with the team has become far easier.
![]()
VIVANTES
Roman Brunka
One of Fudo’s biggest advantages was its functions, especially the simplicity of configuring them each individually. The intelligent interface ensures a clear overview. Dealing and working with the team has become far easier.
![]()






